LDAP
LDAP¶
The application supports authentication via LDAP (Lightweight Directory Access Protocol), which allows users to log in using their directory credentials. The implementation uses the LdapExternalLoginProvider to authenticate users against an LDAP server (typically Active Directory).
The Identity module has built-in OpenLdapManager and ActiveDirectoryLdapManager services. It implements LDAP authentication and gets user info for external login.
The cross-platform LdapForNet library is used for Windows LDAP authentication. See LdapForNet GitHub repository for more information.
Prerequisites¶
- LDAP server (e.g., Active Directory) accessible from your application server
- A service account with permissions to bind to the LDAP server and search for users
- The LDAP feature enabled in your application
How to enable LDAP External Login feature ?¶
You need to enable the LDAP login feature and configure related settings.
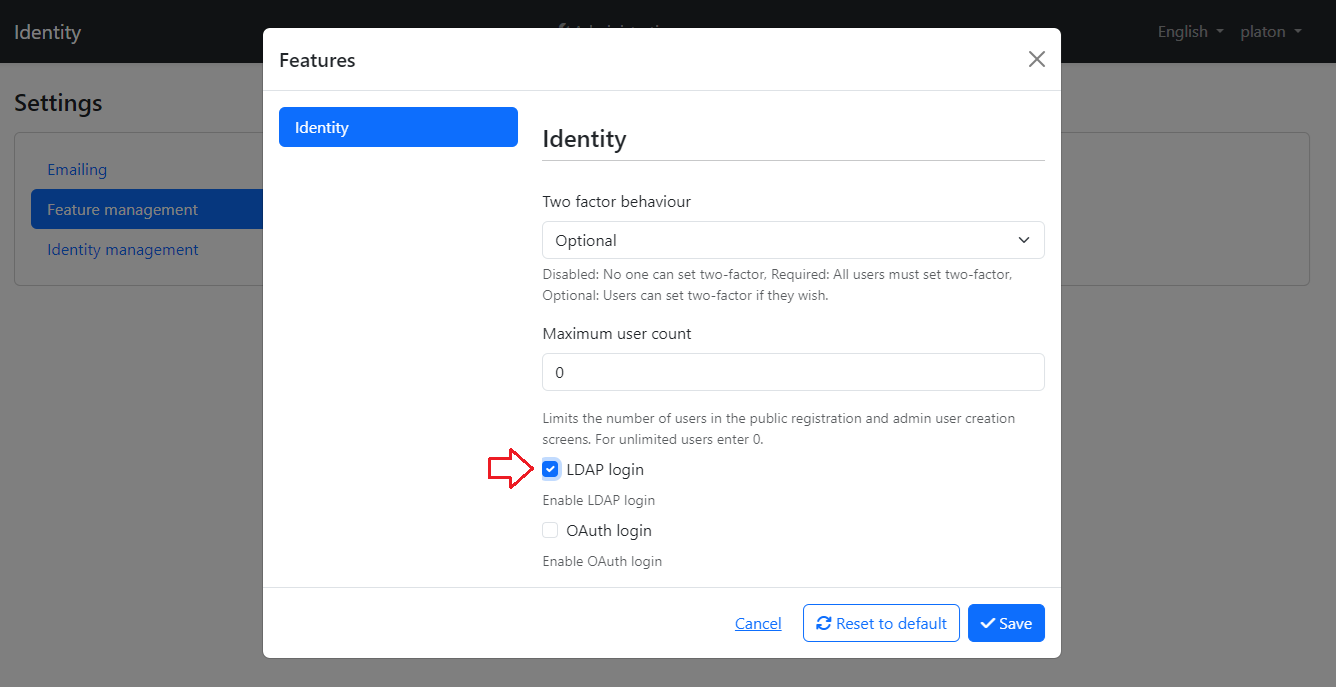
Configuration parameters¶
The following settings need to be configured for LDAP authentication:
| Parameter | Description | Example Value |
|---|---|---|
| EnableLdapLogin | Whether LDAP authentication is enabled | true |
| UseSsl | Whether to use SSL for the LDAP connection (LDAPS) | true |
| TrustAllCertificates | Whether to trust all SSL certificates (not recommended for production) | false |
| Hostname | The LDAP server hostname or IP address | ldap.example.com |
| Port | The LDAP server port (typically 389 for LDAP, 636 for LDAPS) | 636 |
| SearchBase | The base DN to search for users | OU=Users,DC=example,DC=com |
| Domain | The Active Directory domain name | example.com |
| UserName | The username of the service account for binding to the LDAP server | serviceaccount@example.com |
| Password | The password of the service account | (secure password) |
How to Configure ?¶
The LDAP settings can be configured through the application's administration interface or directly in the database through the settings system.

Through the Administration Interface
- Log in as an administrator
- Navigate to the Identity settings section
- Select the LDAP tab
- Enter the required LDAP configuration parameters
- Save the settings
Customize Active Directory Ldap Manager¶
The default ActiveDirectoryLdapManager service uses User Principal Name (UPN) format to normalize user name, and use $"(userPrincipalName={userName})" to search for users, use mail as attribute name to get email.
If your username has a prefix or a specific format, you can override the NormalizeUserNameAsync method of ActiveDirectoryLdapManager to handle it. You can also customize the GetUserFilterAsync and GetUserEmailAsync methods.
[Dependency(ReplaceServices = true)]
[ExposeServices(typeof(ActiveDirectoryLdapManager), typeof(ILdapManager), typeof(LdapManager))]
public class CustomActiveDirectoryLdapManager : ActiveDirectoryLdapManager
{
public ActiveDirectoryLdapManager(ILdapSettingProvider ldapSettingProvider)
: base(ldapSettingProvider)
{
}
protected override async Task<string> NormalizeUserNameAsync(string userName)
{
// or "userName@domain
// await LdapSettingProvider.GetDomainAsync()
return Task.FromResult($"GridLab\\{userName}");
}
protected override Task<string> GetUserFilterAsync(string userName)
{
// Default is $"(userPrincipalName={userName})"
return return Task.FromResult($"(&(objectClass=user)(sAMAccountName={userName}))");
}
protected override Task<string> GetUserEmailAsync(LdapEntry ldapEntry)
{
return Task.FromResult(ldapEntry.ToDirectoryEntry().GetAttribute("mail")?.GetValue<string>());
}
}
Customize OpenLDAP Ldap Manager¶
The OpenLdapManager service uses $"cn={userName},{searchBase}" to normalize user name, and use $"(&(uid={userName}))" to search for users, use mail as attribute name to get email.
The value of
searchBaseis the setting of the "Search base domain component".
If your username has a prefix or a specific format, you can override the NormalizeUserNameAsync method of OpenLdapManager to handle it. You can also customize the GetUserFilterAsync and GetUserEmailAsync methods.
LDAP test application¶
Testing the LDAP configuration using your application might be time-consuming. The following simple Dotnet Console App is for testing your LDAP configuration.
cd app\GridLab.GMSS.Identity.Ldap
Before configuring your LDAP settings, you can test the information via this app to see if it works